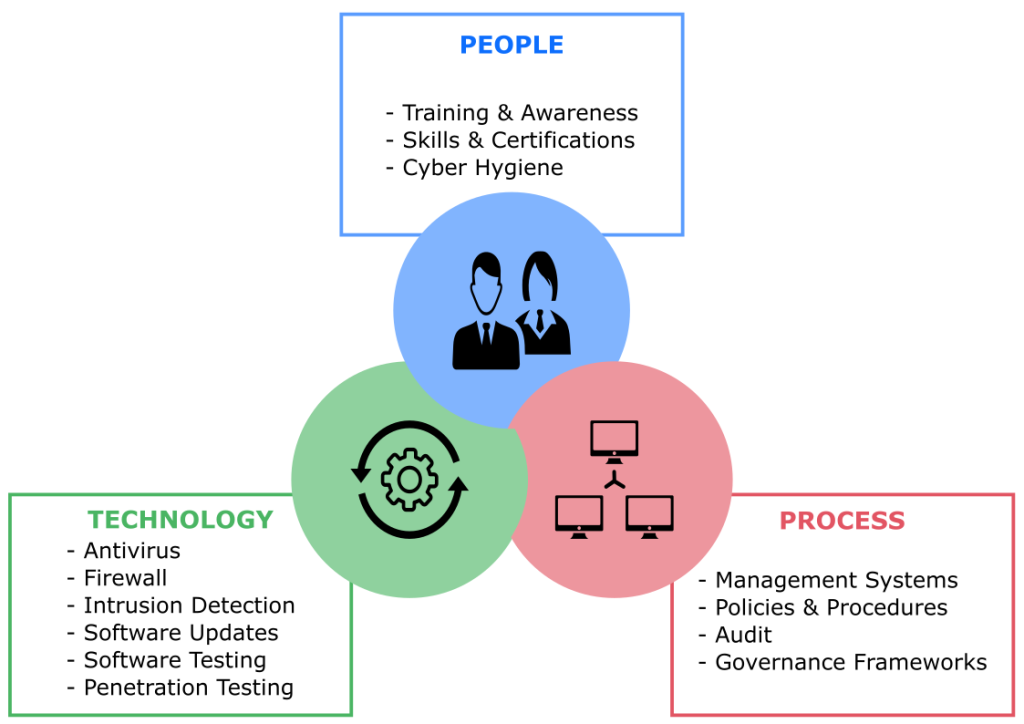
People, Processes, and Technology Security Tactics
There are various approaches that IT teams should consider when attempting to develop a tiered security environment:
People
Employees can pose some of the most serious threats to cybersecurity. They can, however, be an asset and a first line of defense if they are well informed. Employees are frequently targeted as an attack vector by hackers due to their lack of awareness about security best practices. For example, thieves may send phishing emails to employees in order to induce them to click on a dangerous link or divulge credentials. With this in mind, it is critical that firms hold frequent training sessions throughout the year to keep staff informed of potential scams and the ways they can expose their organization to risk.
Training programs like these will foster a strong cybersecurity culture, which will go a long way toward reducing threats. IT departments will seek to inform employees about the following cyber hygiene issues:
Creating strong passwords that are unique to each account and are not reused, as well as separating personal and professional passwords.
Not opening or clicking links in dubious or unknown sender emails.
Ensure that applications and operating systems are constantly updated as soon as patches are issued, and that no unknown outside software is installed, as this can expose security vulnerabilities in the network.
Reporting any suspicious behavior or strange occurrences on their laptops as soon as possible.
Another method IT teams may strengthen employee cybersecurity is through access control policies such as the principle of least privilege, which allows a worker to access data only when it is required to complete their job, lowering the exposure and consequences of a breach.
Processes
First and foremost, IT security teams must have a cyber event response plan in place. A solid incident response plan will give an organization with repeatable procedures and an operational approach to dealing with cybersecurity problems so that business processes can be recovered as fast and efficiently as feasible. Furthermore, ensuring proper backups are in place and checking these backups on a regular basis is critical to avoiding downtime and boosting the odds of data recovery from a cyber event.
The next step is to collect and analyze threat research. To effectively detect and respond to attacks, every security strategy and instrument must be informed by current threat intelligence. Threat analysis, for example, may disclose that cybercriminals have been carrying out attacks using a certain vulnerability or targeting endpoints with a specific malware. Armed with this knowledge, IT professionals can take preemptive precautions such as doing any necessary system updates and enhancing monitoring to spot behavior indicative of one of these assaults. It is also critical that IT teams study both local and global threat data to gain a complete picture of the threat landscape.
Prioritization of assets is another critical step on the path to effective cybersecurity. While IT personnel continue to be overburdened as a result of the cybersecurity skills gap, networks have gotten increasingly sophisticated, making it hard to manually monitor every section of the network at all times. As a result, IT teams must be aware of the location of all their assets and prioritize them depending on those are the most business vital and would have the largest impact on the business if compromised. Security teams can then establish policies and methods to make this data more safe and limit the effects. This could imply utilizing network segmentation to add an extra layer of protection or developing access control policies based on who requires access to which data sets.
Technology
As previously noted, security teams can layer their protections by implementing a variety of technologies. However, it is critical that IT teams do not adopt isolated point solutions as they layer their defenses, but rather choose tools based on their potential to be integrated and automated to form a Security Fabric that can assist rapid detection and mitigation of threats.
Another strategy that IT teams should employ is deception technology. Adversaries’ Achilles’ heel is network intricacy. Deception technologies level the playing field by automating the generation of dynamic decoys spread throughout the IT environment, making it more difficult for adversaries to distinguish which assets are phony and which are real. When an adversary is unable to establish this distinction, cybercriminals are forced to waste time on bogus assets and practice caution while searching for tripwires placed in bogus settings. This may necessitate them changing their approaches, increasing their chances of being identified by security teams.
Finally, IT departments should make use of segmentation. Adversaries target networks in order to obtain access to and exploit organizations’ vital data, such as customer and personnel information, intellectual property, financial records, and so on. IT teams can segregate their apps and sensitive data into different segments of subnetworks with varied degrees of security by segmenting corporate networks. This enables stronger access control on vital systems, limiting exposure in the event of a compromise.
Last Thoughts
Modern network security necessitates a multi-layered protection strategy that considers people, procedures, and technology. Such approaches, which include developing a strong security culture, undertaking threat analysis, prioritizing assets, and adopting contemporary network controls, will improve visibility and reduce the effect of intrusions.
Be First to Comment